NIST Framework 2.0: A Comprehensive Overview
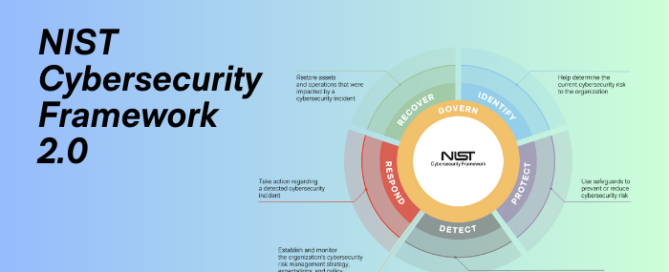
Today, the security of sensitive information and digital assets is a top priority for organizations globally. The National Institute of Standards and Technology (NIST) Cybersecurity Framework 2.0 stands as a potent and adaptable instrument, aimed at aiding organizations of varying sizes in navigating the intricate terrain of cybersecurity. Developed by NIST, a renowned authority in











Follow us on: