WHY ERMES ADVANCED URL FILTERING
Cybersecurity remains a paramount concern for every organization. The constantly evolving online threats pose significant challenges to productivity
and security. This is where our “Advanced URL filtering” solution, a key component of the ERMES BROWSER SECURITY platform, sets itself apart from the rest.
We provide you with an intelligent solution that extends beyond traditional boundaries. Our solution ensures that policies remain effective even beyond
the network perimeter, offering enhanced control and security. Moreover, our system allows for granular policy customization, enabling you to tailor access restrictions to specific user groups, thereby ensuring comprehensive security and productivity organization-wide.
Our “Advanced URL filtering” solution skillfully manages website access by analyzing content, enhancing security and productivity. With Ermes, you can customize access policies, extend security beyond the corporate network, maintain visibility even when dealing with web proxies and translation services, and benefit from AI-driven threat detection. Our user-centered approach and seamless integration empower businesses to flourish in a secure digital environment, enabling them to thrive with confidence.
Enforces company policies through tailored content filtering



The Ermes Browser Security technology
is cutting-edge and offers you a range
of unique advantages
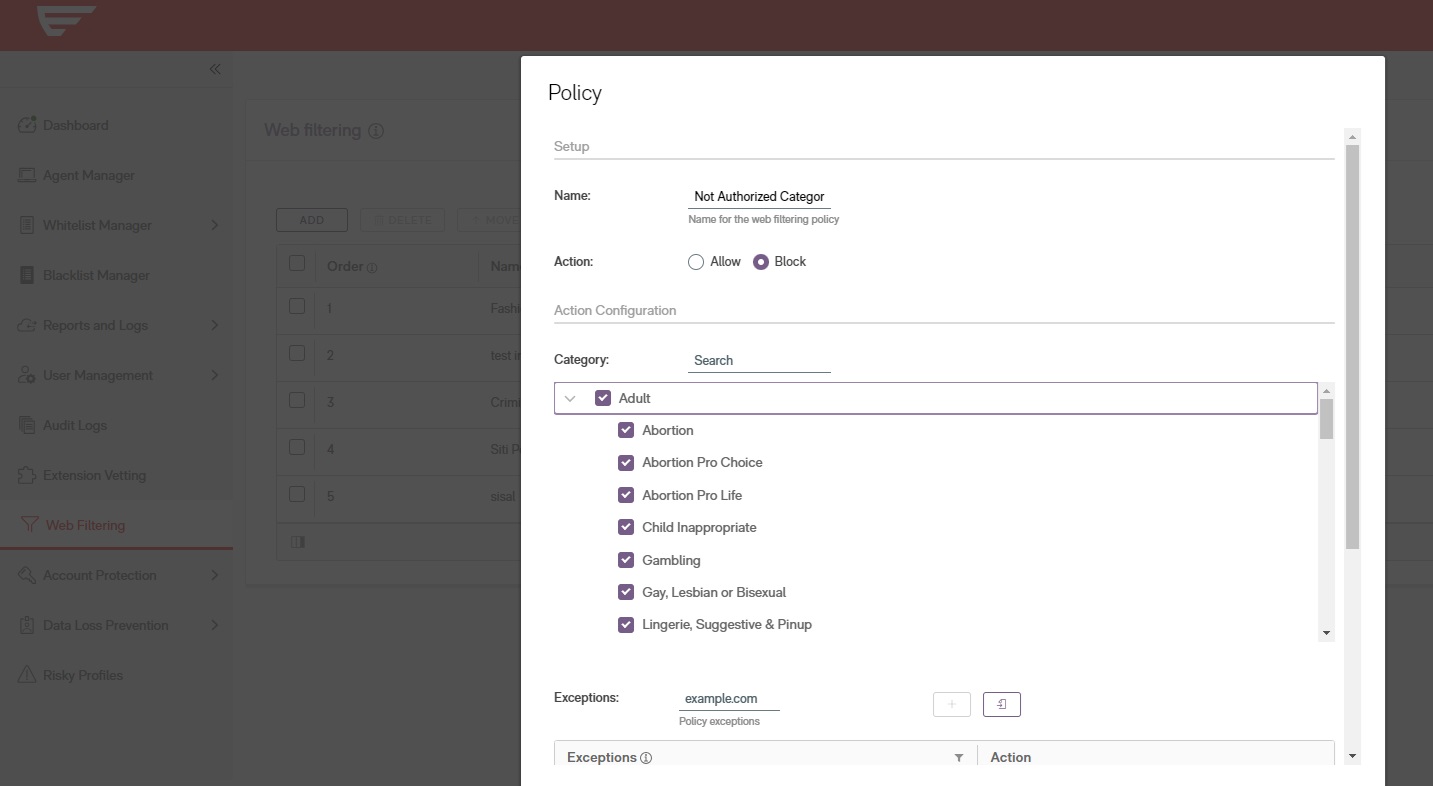
Policy
Management
With our Content Filter, you can create customized access policies. For example, you can prohibit the use of social networks during working hours for all users, except for the marketing department, which requires them for work purposes.
Access Beyond the
Corporate Perimeter
Our policies are valid even outside the corporate environment, without the need for a VPN. This means your employees can securely work from anywhere.
Advanced
Visibility
Our advanced architectural positioning allows us to correctly apply policies even when content is accessed through translation services, web proxies, and anonymization services. These methods are often used by users to bypass traditional blocking systems.



Follow us on: