Online VPN, what is it and why is it important? Nowadays, online data security has become an absolute priority. Virtual Private Networks (VPNs) emerge as essential tools in this context, offering a reliable solution to protect your privacy and personal data. This article explores the vital role of VPNs in safeguarding digital information, outlining how these private networks can effectively defend against online threats and ensure secure browsing.
What is a VPN?
A VPN, or Virtual Private Network, is a crucial tool for online security that allows you to browse the Internet safely and privately. It works by creating an encrypted tunnel between your device and a remote server managed by the VPN provider. This tunnel acts as a virtual shield, hiding your real IP address and replacing it with that of the VPN server. This way, all your online activities pass through this secure tunnel, making it nearly impossible for hackers, Internet service providers, and even governments to monitor or intercept your data. Using a VPN also means being able to access geographically restricted content, as you can appear as if you are connected from another part of the world. In short, a VPN is a fundamental defense for your online privacy and security, protecting your personal data and enabling unprecedented browsing freedom.
How Does a VPN Work?
A VPN works by creating a secure and encrypted tunnel between your device and the Internet. This tunnel prevents third parties from intercepting or spying on your web traffic, ensuring your online privacy and security. When you activate a VPN, your Internet traffic is sent through a VPN server. This process not only encrypts your data but also masks your real IP address, replacing it with that of the VPN server. As a result, your online location appears different, allowing you to bypass geographical restrictions and censorship. Additionally, the VPN acts as a filter, protecting your sensitive data from prying eyes, whether you are browsing from home or connected to a public Wi-Fi network. In essence, a VPN provides a level of security and anonymity crucial in the digital age, safeguarding your digital identity and personal data from potential online threats.
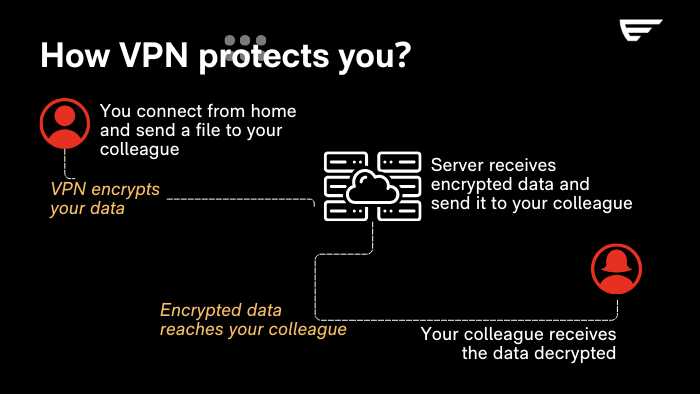
Data Encryption
Data encryption is the lifeblood of a VPN, acting as an impenetrable shield for your online privacy. When you activate a VPN, your data is immediately encrypted, transforming it into an indecipherable code for anyone attempting to intercept it. This process uses sophisticated algorithms to ensure that the information transmitted between your device and the VPN server remains private and secure. Whether you are sending emails, browsing websites, or conducting banking transactions, VPN encryption protects every bit of data, making each of your digital actions secure and private. In an era where data security is paramount, the encryption offered by VPNs serves as a crucial defense against cybersecurity threats.
Connecting to the VPN Server
Connecting to the VPN server is a crucial step in the security process. When you activate the VPN, your device establishes a secure connection with a chosen server. This server can be located anywhere in the world, allowing you to “appear” as if you are connected from that specific location. This process not only masks your real location but also encrypts all the data you send and receive. This way, even if your data were to be intercepted during transmission, it would be indecipherable to anyone without the decryption key. This secure connection is essential to protect your online privacy and prevent your Internet activities from being monitored or traced by unauthorized third parties.
Substitute IP Address
A fundamental aspect of the security provided by VPNs is the ability to provide a substitute IP address. When you connect through this service, your real IP address is masked and replaced with that of the VPN server. This process not only hides your actual geographical location (as mentioned before) but also makes it more challenging for websites, advertisers, and potential malicious actors to track your online activity. In practice, the substitute IP address acts as a digital camouflage, significantly enhancing your online privacy. This feature is particularly useful for avoiding online surveillance and censorship, allowing you to browse freely and without geographical restrictions. Moreover, it protects your digital identity from potential cyberattacks, making the VPN an essential tool for anyone wishing to maintain a high level of anonymity and online security.
Utility of VPNs in Data Protection
VPNs are not just a means to access geographically restricted content; they represent a crucial component in the protection of personal and business data. In an era where data security is increasingly threatened by cyber-attacks and privacy breaches, VPNs offer an essential level of security. By encrypting data transmitted over the Internet, these services prevent sensitive information such as banking details, passwords, and personal data from falling into the wrong hands. This is particularly important when using public Wi-Fi networks, known to be vulnerable to intrusions and man-in-the-middle attacks. Additionally, VPNs help maintain online anonymity, protecting users from unwanted tracking and profiling. In summary, using a VPN is a fundamental step for anyone wishing to browse the Internet not only freely but also safely and securely.
What are the Disadvantages of a VPN?
Despite the numerous advantages offered by VPNs, it is essential to consider some disadvantages that may impact your online experience:
- Reduced Connection Speed: Data encryption can slow down your Internet connection due to the time required to encrypt and decrypt data, as well as the longer path data must travel through the VPN server.
- Cost: While free VPNs exist, they often offer limited services and may compromise your privacy. High-quality VPNs require a subscription, representing an additional cost for the user.
- Configuration Complexity: For the less tech-savvy, configuring and using a VPN can be challenging. Choosing the right server and configuring settings require a certain level of technical knowledge.
- Legal and Geographical Limitations: In some countries, the use of VPNs is regulated or even prohibited. It is crucial to be aware of local laws before using a VPN.
- False Sense of Security: A VPN protects your Internet connection, but it is not a complete solution for online security. Users must still adopt good security practices, such as using strong passwords and being cautious when opening suspicious emails.
Considering these aspects will help you make an informed choice about using a VPN and better understand how to integrate it into your digital security strategy.
Determining if You Need a VPN
Assessing the need for a VPN depends on various factors related to your online activities and your concern for privacy. If you frequently connect to public Wi-Fi networks, this service is almost indispensable to protect your data from prying eyes. Additionally, if you want to access geographically restricted content or bypass censorship in certain countries, a VPN can be the ideal solution. For remote workers, a VPN ensures a secure and protected connection, essential for safeguarding sensitive business information. Finally, if your priority is maintaining online anonymity and preventing tracking by ISPs and websites, using a VPN becomes a crucial element. In summary, if your online activity requires a high level of privacy, security, and freedom, adopting a VPN is a wise and informed choice.
5 Reliable VPNs to Consider
Here is a list of 5 reliable VPNs you can consider to protect your Internet connection:
- ExpressVPN: With a wide network of servers worldwide and high speeds, ExpressVPN offers a stable and secure connection during travels. It also supports a wide range of devices and provides advanced encryption to ensure your online privacy.
- NordVPN: The service is known for its robust encryption and its ability to unlock geographically restricted content. It offers a vast network of global servers and advanced security features, such as double encryption and protection against DNS leaks.
- CyberGhost: CyberGhost is an easy-to-use VPN with an intuitive interface. It offers robust protection, a vast network of servers, and features for unblocking geographically restricted content. It is particularly suitable for beginners or those looking for a user-friendly option.
- Surfshark: Surfshark is a relatively new but rapidly growing VPN. It offers excellent encryption, high speeds, and the ability to connect to an unlimited number of devices simultaneously, ideal for travelers with multiple devices.
- Private Internet Access (PIA): PIA is a reliable service with an excellent zero-log policy, meaning it does not record your browsing activities. It also offers a wide range of servers worldwide and provides good value for money.
There is the possibility to avoid the use of a VPN. In fact, Ermes Cyber Security, thanks to its own Add-On, allows you to avoid installing additional tools. Discover our solutions.
Mistakes to Avoid When Using a VPN
Using a VPN requires a certain awareness to avoid common mistakes that can compromise your online security. First and foremost, avoid using free VPNs. Often, these versions do not offer the same security as paid options and may even sell your data to third parties. Additionally, it is crucial to keep the VPN always active. Turning it off, even temporarily, exposes your data to potential risks, especially on public networks. Another common mistake is ignoring the VPN’s log policy. Ensure that your VPN has a verified no-log policy to ensure that your online activities are not recorded. Finally, do not underestimate the importance of a strong password and sound online security practices. Even the best VPN cannot protect you from weak passwords or reckless online behaviors.
In conclusion, VPNs are powerful tools to enhance your online security, but only if used correctly. Choosing a reliable VPN, keeping it always active, paying attention to the log policy, and following good online security practices are crucial steps to ensure the protection of your data. Remember, online security starts with you.


Follow us on: